Abstract
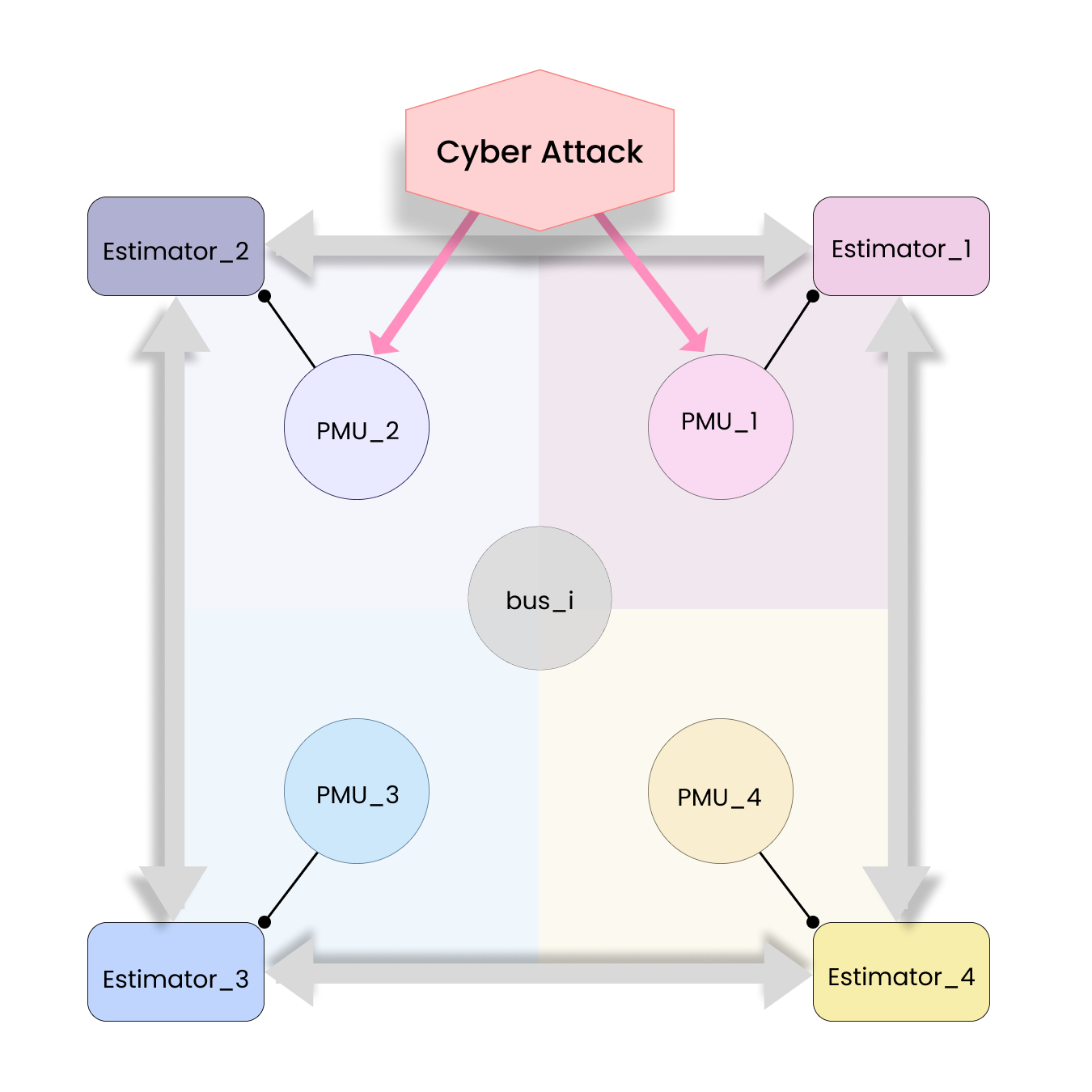
Cyber security in power systems has become increasingly critical with the rise of network attacks such as Denial-of-Service (DoS) attacks and False Data Injection (FDI) attacks. These threats can severely compromise the integrity and reliability of state estimation, which are fundamental to the operation and control of power systems. In this manuscript, an estimation algorithm based on the fusion of information from multiple estimators is proposed to ensure that state estimation at critical buses can function properly in case of attacks. Our approach leverages a network of estimators that can dynamically adjust to maintain system stability and accuracy. Furthermore, a new detector is adopted based on Kullback-Leibler divergence to detect linear FDI attacks. To address stealthy attacks that may evade detection, we propose a novel weighting scheme that reduces the impact of attacks on estimation results. Numerical experiments demonstrate the effectiveness and accuracy of our proposed estimation algorithm under cyber attacks.
Keywords
state estimation
smart grid
data fusion
Kullback-Leibler divergence
cyber attack
Funding
This work was supported in part by the National Key R&D Program of China under Grant 2023YFF1204805; in part by the National Natural Science Foundation of China under Grant 62336005, Grant 62122026; in part by the projects sponsored by the Programme of Introducing Talents of Discipline to Universities (the 111 Project) under Grant B17017; and in part by the Shuguang Program supported by Shanghai Education Development Foundation and Shanghai Municipal Education Commission.
Cite This Article
APA Style
Jin, S., Yang, W., Yuan, H., Ding, W., Wu, H. & Wang, J. (2024). Robust Distributed State Estimation in Power Systems: A Multi-Estimator Data Fusion Approach to Counteract Cyber-Attacks. Chinese Journal of Information Fusion, 1(3), 212–225. https://doi.org/10.62762/CJIF.2024.740709
Publisher's Note
IECE stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Institute of Emerging and Computer Engineers (IECE) or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue