Abstract
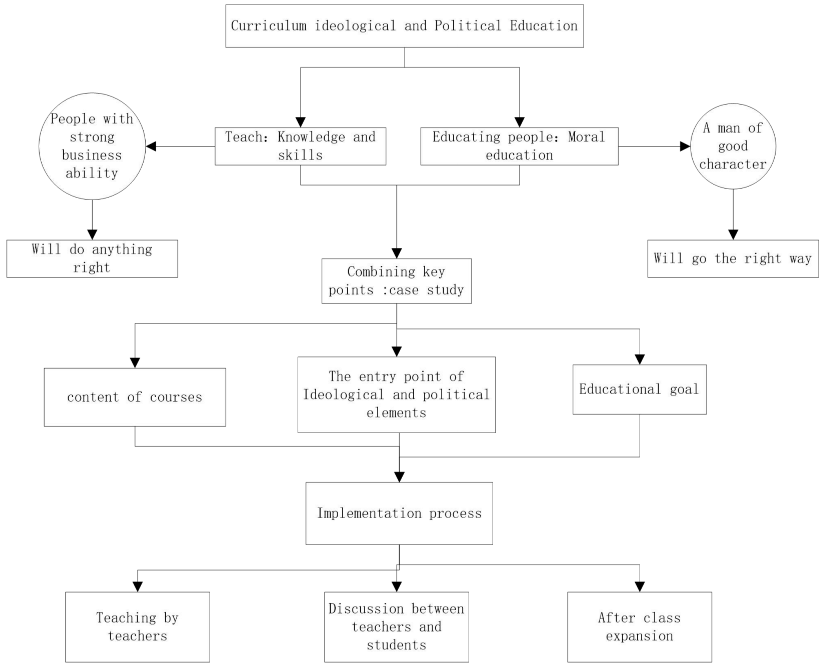
In alignment with the objective of integrating ideological and political education within curricula, this study uses the "Information Security" course as a model to illustrate the approach of embedding core ideologies pertinent to the forefront of international scientific application, national key needs, and the primary battlegrounds of the economy. By weaving frontier science and technology along with national security regulations into the educational practice, this research delves into teaching cases within the information security domain to construct a curriculum system that seamlessly integrates ideological, political, and academic content. The system aims to foster the cultivation and practice of socialist core values, guiding students towards proper personal and professional conduct. This abstract presents a methodology for curriculum reform that not only enriches academic content but also instills ethical and social responsibilities in students, contributing to the holistic development of future professionals.
Keywords
curriculum ideological and political education
information safety
curriculum system
Funding
This work was supported by 2019 Shaanxi higher education teaching reform research project "ideological and political research and practice of 'information security' course in the era of big data" of funding agency under Grant 19BY135.
Cite This Article
APA Style
Zheng, P., Wang, X.,& Li, J. (2024). Reforming Curriculum Ideology and Political Construction: A Case Study of the ’Information Security’ Course. IECE Transactions on Computer Science, 1(1), 26–31. https://doi.org/10.62762/TCS.2024.210691
Publisher's Note
IECE stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Institute of Emerging and Computer Engineers (IECE) or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue