Abstract
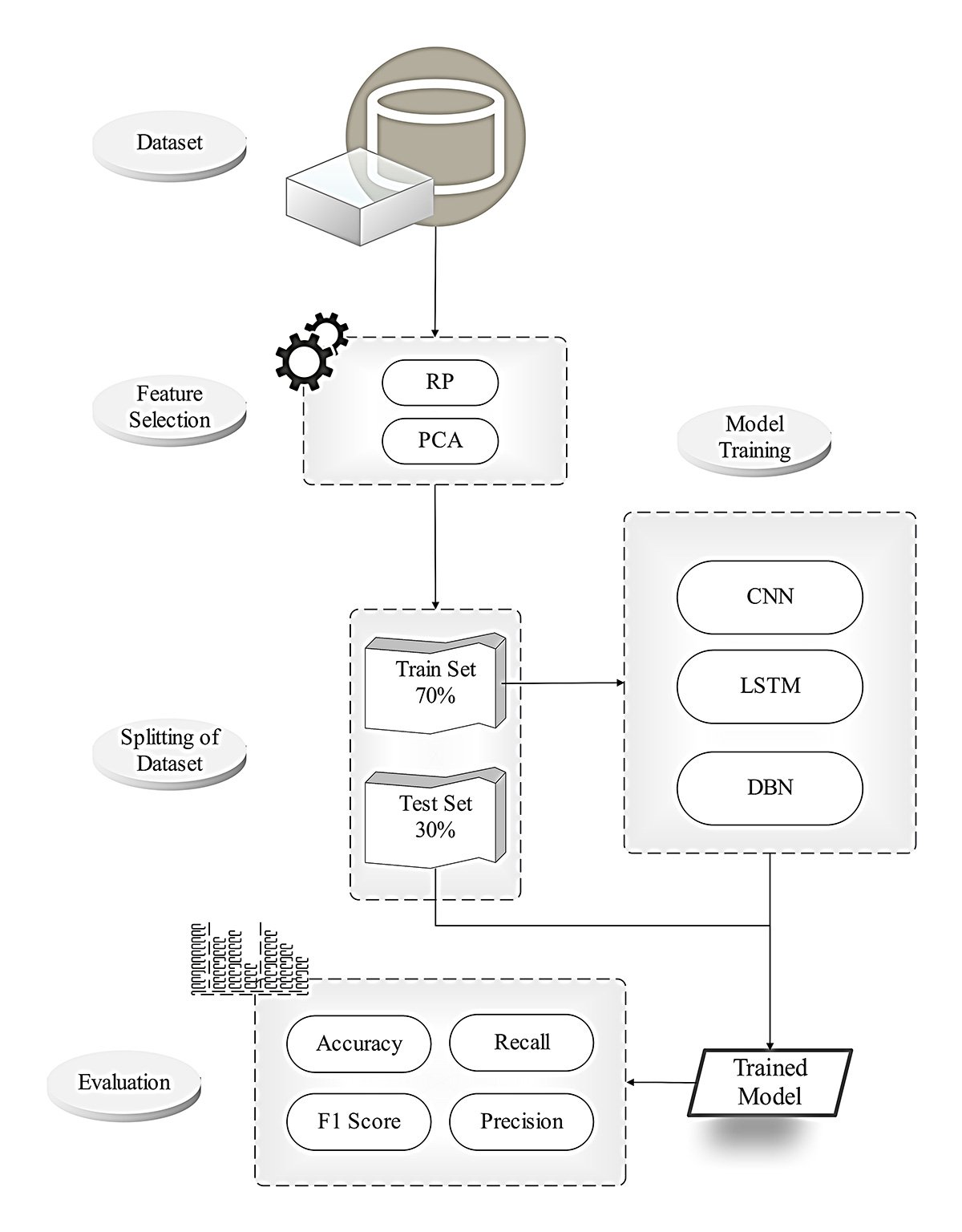
In recent years, vehicular ad hoc networks (VANETs) have faced growing security concerns, particularly from Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks. These attacks flood the network with malicious traffic, disrupting services and compromising resource availability. While various techniques have been proposed to address these threats, this study presents an optimized framework leveraging advanced deep-learning models for improved detection accuracy. The proposed Intrusion Detection System (IDS) employs Convolutional Neural Networks (CNN), Long Short-Term Memory (LSTM), and Deep Belief Networks (DBN) alongside robust feature selection techniques, Random Projection (RP) and Principal Component Analysis (PCA). This framework extracts and analyzes significant features using a publicly available application-layer DoS attack dataset, achieving higher detection accuracy than traditional methods. Experimental results indicate that combining CNN, LSTM networks, and DBN with feature selection techniques like Random Projection (RP) and PCA results in improved classification performance, achieving an accuracy of 0.994, surpassing the state-of-the-art machine learning models. This novel approach enhances the reliability and safety of vehicle communications by providing efficient, real-time threat detection. The findings contribute significantly to VANET security, laying a robust foundation for future advancements in connected vehicle protection.
Keywords
vehicular networks security
denial of service (DoS) detection
deep learning intrusion detection
feature optimization techniques
connected vehicle protection
Funding
This work was supported without any funding.
Cite This Article
APA Style
Khan, F. M., Rahman, T., Zeb, A., Haider, Z. A., Khan, I. U., Bilal, H., Khan, M. A. & Ullah, I. (2024). Vehicular Network Security Through Optimized Deep Learning Model with Feature Selection Techniques. IECE Transactions on Sensing, Communication, and Control, 1(2), 136–153. https://doi.org/10.62762/TSCC.2024.626147
Publisher's Note
IECE stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
IECE or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue