IECE Transactions on Computer Science
ISSN: request pending (Online)
Email: [email protected]


 Submit Manuscript
Edit a Special Issue
Submit Manuscript
Edit a Special Issue
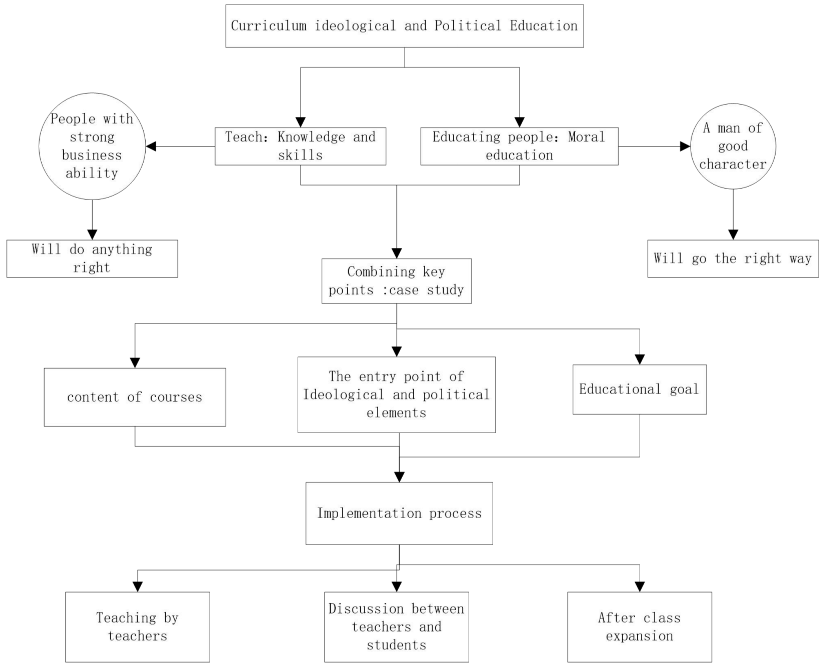
[1] Hu Aiqun, Li Guyue, Peng linning, Li Tao. Teaching exploration of Cyberspace Security Frontier Technology integrated with ideological and Political Education [J]. Journal of network and information security, 2019, 5(3):54-66.
[2] Xu Jianguang. Adhere to the whole curriculum education and deepen the curriculum ideological and political reform [J]. Shanghai Education, 2017 (12):14-14.
[3] Liu Lei, Liu Li. Connotation and significance of "Three Orientations" science and technology policy [J]. Global science and technology economy outlook, 2018, 33 (11):25-30.
[4] Si Jin. Exploration and practice of Ideological and political education in professional and technical courses [J]. Computer age, 2020, 332 (02):98-100.
[5] Ding Zhiguo. Exploration on the teaching reform of science and engineering courses from the perspective of "Curriculum Ideology and politics" – Taking "software quality assurance and testing" as an example [J]. China information technology education, 2020, 334 (10):101-103.
[6] Feng Jianwen, Miao Liming. Reform and practice of Ideological and political education of software engineering course in Colleges and universities [J]. Education modernization, 2020, 7 (01):29-31.
[7] Lu Yulin. Thinking on the collaborative education of various courses and ideological and political theory courses [J]. Science and education Wenhui, 2017, 12 (34):32-33.
[8] Bai Yinhua. Effective ways to enhance the affinity of Ideological and political theory courses in Colleges and Universities under the new situation [J]. Changjiang series, 2017 (28):250.[9] Hu Aiqun, Li Guyue, Peng linning, Li Tao. Teaching exploration of Cyberspace Security Frontier Technology integrated with ideological and Political Education [J]. Journal of network and information security, 2019, 5(3):54-66.
[10] Xu Jing. Teaching reform and practice of Ideological and political education in the course of introduction to information security guided by law-abiding [J]. Education modernization, 201, 6 (59):66-68.
[11] Wang, Y., Li, H., & Li, X. (2017). A case of on-chip memory subsystem design for low-power CNN accelerators. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 37(10), 1971-1984.
[12] Liu, C., Chu, C., Xu, D., Wang, Y., Wang, Q., Li, H., ... & Cheng, K. T. (2021). HyCA: A hybrid computing architecture for fault-tolerant deep learning. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 41(10), 3400-3413.
[13] Xu, D., Chu, C., Wang, Q., Liu, C., Wang, Y., Zhang, L., ... & Cheng, K. T. (2020, October). A hybrid computing architecture for fault-tolerant deep learning accelerators. In 2020 IEEE 38th International Conference on Computer Design (ICCD) (pp. 478-485). IEEE.
[14] Ma, X., Wang, Y., Wang, Y., Cai, X., & Han, Y. (2022). Survey on chiplets: interface, interconnect and integration methodology. CCF Transactions on High Performance Computing, 4(1), 43-52.
[15] Wu, B., Wang, C., Wang, Z., Wang, Y., Zhang, D., Liu, D., ... & Hu, X. S. (2020). Field-free 3T2SOT MRAM for non-volatile cache memories. IEEE Transactions on Circuits and Systems I: Regular Papers, 67(12), 4660-4669.


Portico
All published articles are preserved here permanently:
https://www.portico.org/publishers/iece/