IECE Transactions on Advanced Computing and Systems | Volume 1, Issue 1: 48-62, 2025 | DOI: 10.62762/TACS.2025.835144
Abstract
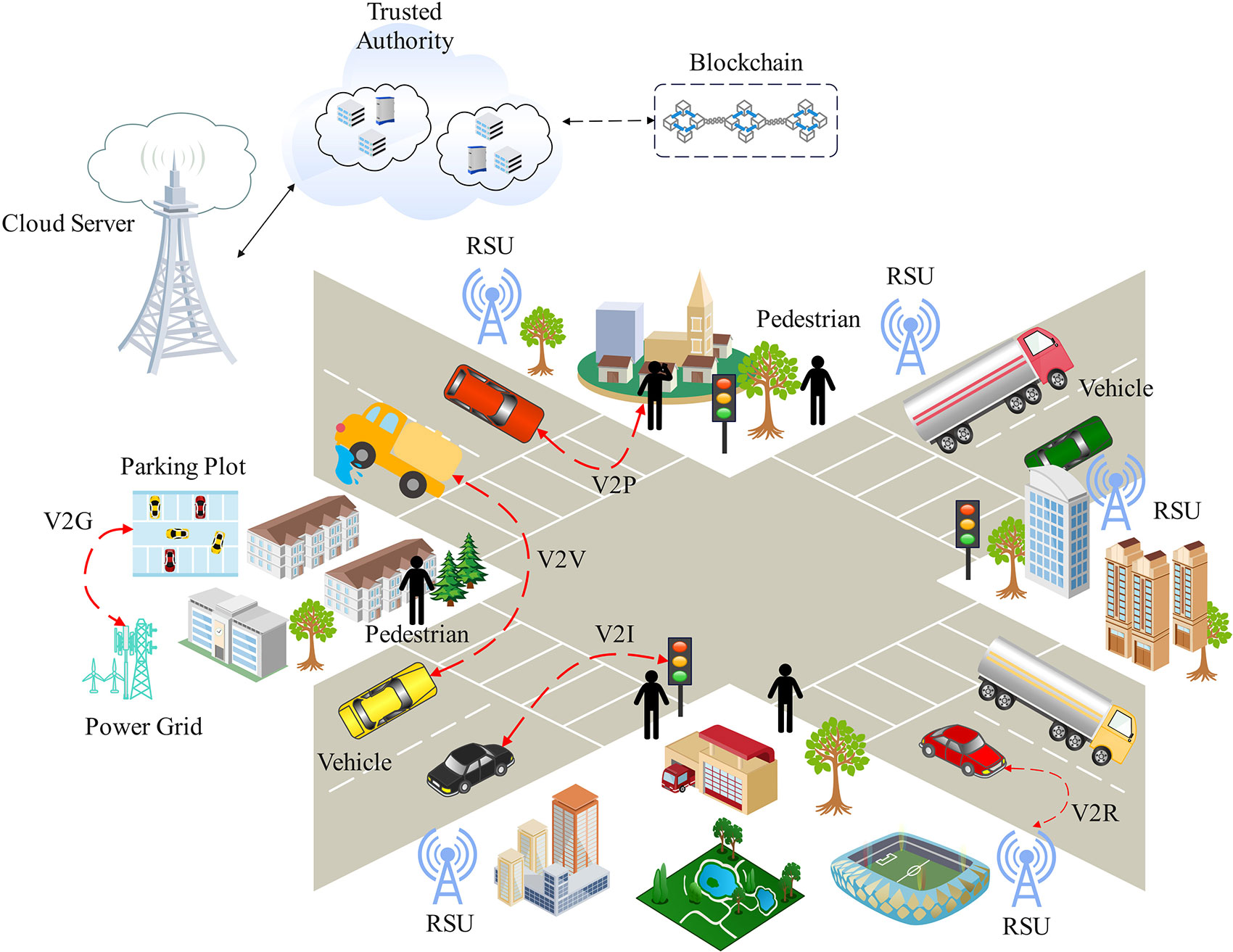
The Internet of Vehicles (IoVs) is an emerging technology that enhances transportation systems by enabling interactions between vehicles, infrastructure, and other entities. Securing IoV networks from cyber threats like eavesdropping, data tampering, and intrusions is a major challenge. This research presents a Blockchain-Enabled Secure Authentication Protocol for IoVs (BESA-IOV), which leverages blockchain’s decentralized and tamper-resistant nature for secure communication in vehicular networks. By utilizing ECC-based lightweight cryptography and blockchain-based public key management, it ensures strong authentication, confidentiality, and integrity. The results show that BESA-IOV signif... More >
Graphical Abstract