IECE Transactions on Advanced Computing and Systems | Volume 1, Issue 1: 32-47, 2025 | DOI: 10.62762/TACS.2024.521915
Abstract
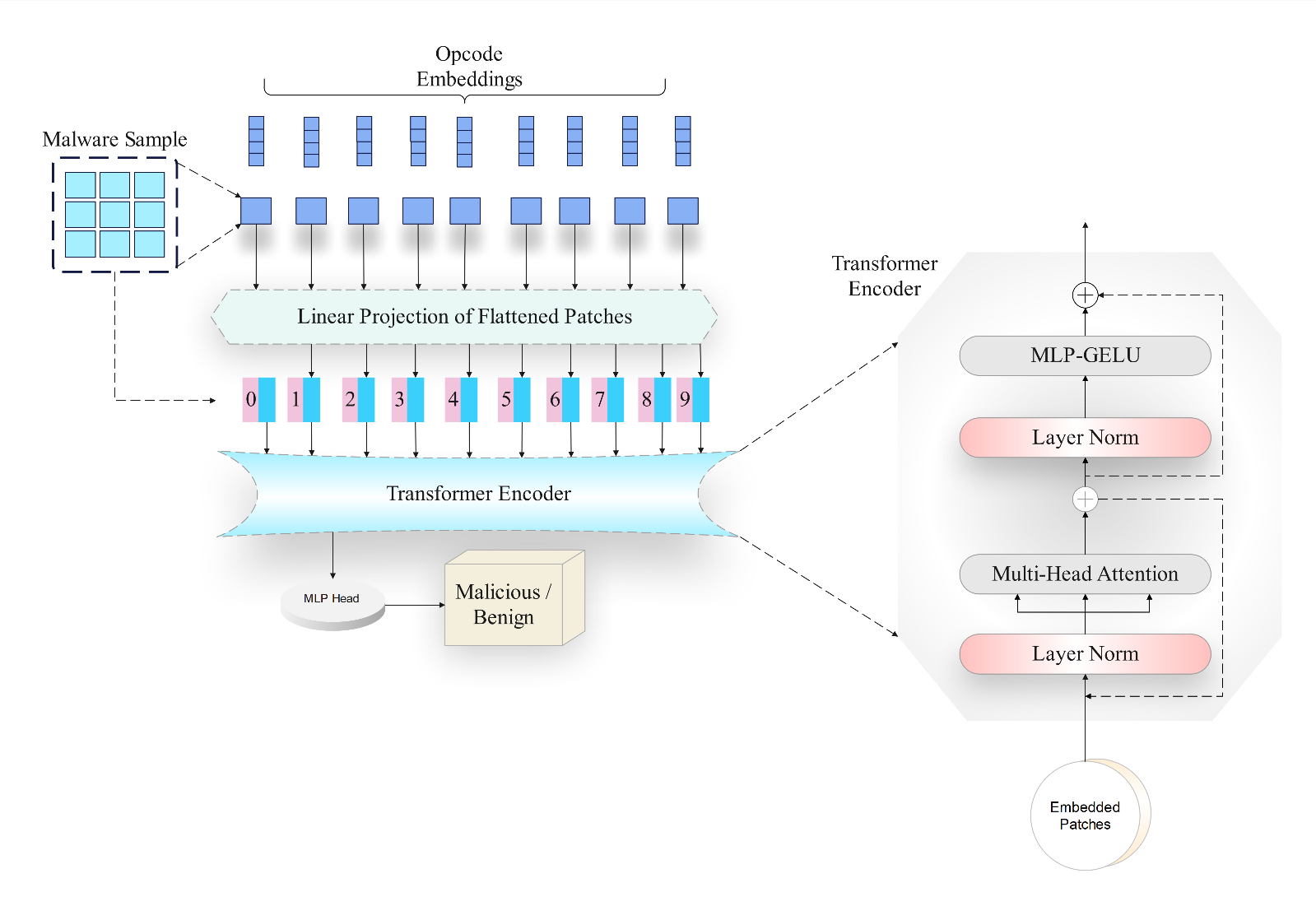
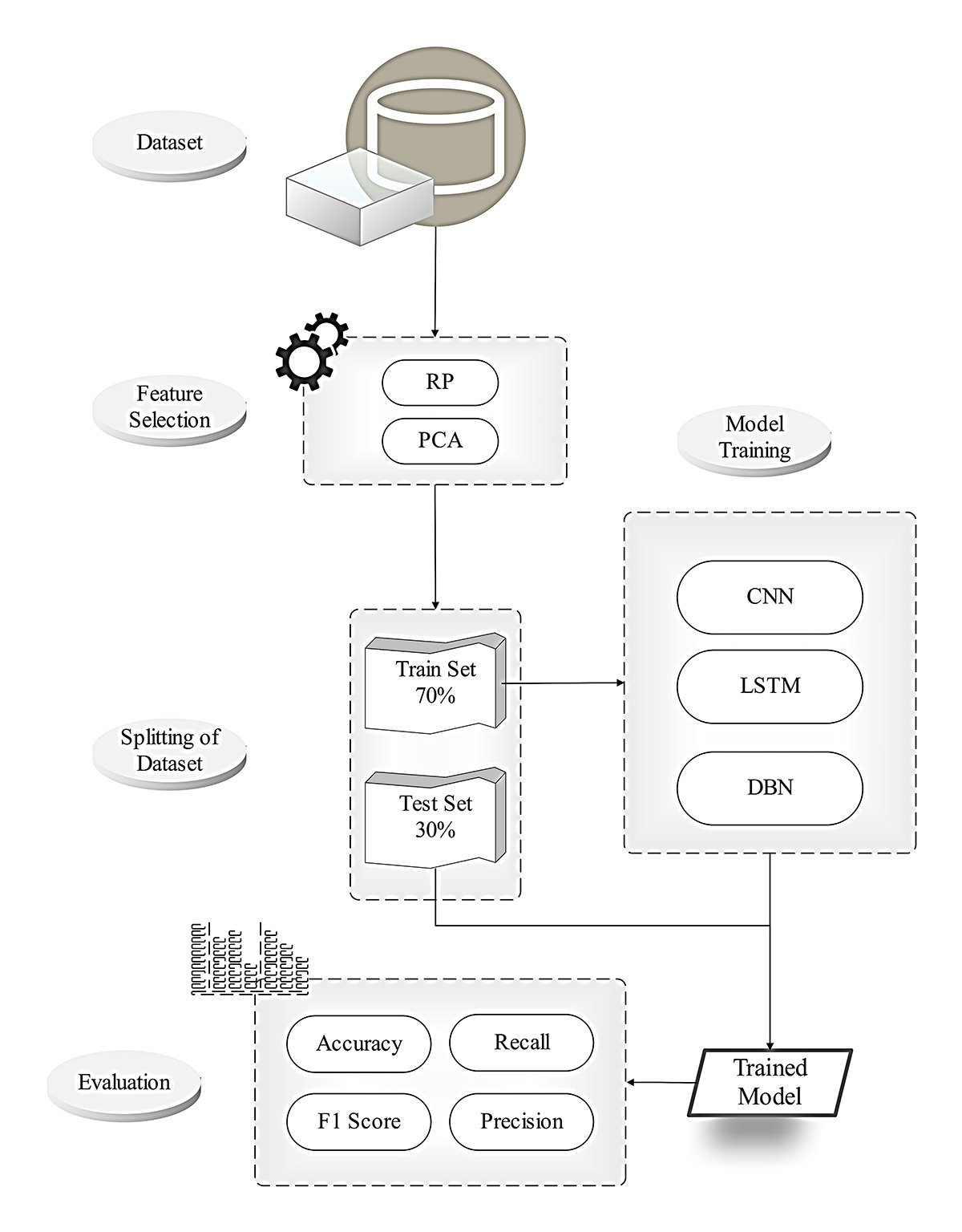
This paper introduces ViTDroid, a novel hybrid model that combines Vision Transformers (ViTs) and recurrent neural networks (RNNs) to enhance Android and IoT malware detection. ViTDroid addresses critical challenges by leveraging ViTs to capture global spatial dependencies and RNNs (LSTM and GRU) to model temporal patterns, enabling comprehensive analysis of complex malware behaviors. Additionally, the model integrates explainability tools, such as LIME and SHAP, to enhance transparency and trustworthiness, essential for real-world cybersecurity applications. The study evaluates ViTDroid's performance against conventional models, including RNN, LSTM, and GRU, using accuracy, precision, recal... More >
Graphical Abstract